
As Darwinbox continue to grow our business nothing is more important that safeguarding our infrastructure and platform, especially with the steadily increasing number of threats. A study at the University of Maryland notes that hackers attack every 39 seconds, on average 2,244 times a day and over 9.7 Million health care records are exposed in September 2020 alone.
At Darwinbox, we scale security through automation. This is an effective way to monitor our infrastructure and detect security drift. As a part of our next generation security automation and tooling. After we reached a level of maturity, we are now shifting gears to advance to the next level of security scale and move from reactive remediation to proactive prevention. In other words, we wanted to ‘secure the HRMS SaaS platform by default’ through enhanced policy and controls that reinforce our existing cloud workload protections.
We automate as much as possible to continue to enhance Darwinbox cloud security and configuration standards. This is especially needed as Darwinbox platform footprint continues to grow and involves multi-cloud environments and technologies such as containers, Kubernetes, Istio and other orchestrators.
To enforce security at all layers of the product, we created a framework which is helping us in deploying right tools and in identifying immediate areas of vulnerability mitigations. The workflow in the framework enforces our teams to implement security tooling and policies efficiently, securely provisioning new account and providing them with hardened container images, secure login to infrastructure, tools to store secrets securely and more. We have policy-based security controls embedded into the framework which controls security against configurations on resources being added to the product.
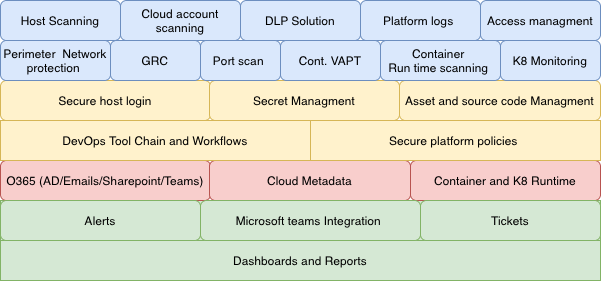
While logging and monitoring provide a human interface to threat reporting, A combination of enterprise tools managed by SOC team ensure threat mitigation by default on below 5 layers of technology stack where Darwinbox Security framework is deployed to collect, analyze, monitor, alert and prevent deviations from default definitions.
Public cloud security:
At Darwinbox we do not rely solely on individuals and manual memory to ensure every setting in our complex public cloud environments are operating error-free. That is why system level controls that operate effectively are standardized and automated across all layers of tech stack. We see number of benefits including its ability to proactively prevent creation of cloud resources that would violate security controls. These controls and tools bring automated decision making and remediation into the security process. Darwinbox uses Terraform templates to orchestrate our cloud Infrastructure and secure SDLC process is fallowed for evert change that is introduced in the cloud echo system.
Cloud SIEM tools play a key role in capturing events related to configurations drifts in cloud environments.
Container Security:
At Darwinbox we started our journey with container-based offering early in the journey, platform architectural designs and decisions were made considering all complex requirements that are needed to provide a secure and reliable platform on container orchestrators like Kubernetes.
Darwinbox platform security frameworks and customized policies in service mesh (Istio) enables SOC team with capabilities to enforce rate limiting, policy bases traffic routing and error injections in every individual microservices and API. Any container that is serving customer data is protected with a side car container doing traffic filtering along with publishing events to SIEM tool.
Platform Security:
While cloud Infrastructure and container security are protected using Darwinbox platform security framework and techniques explained above, in a SaaS echo system the choice of data that a customer can publish on the platform is unique and a predefined policy would not suffice to monitor data leaks and configurations drifts. Below are few parameters of Darwinbox platform security framework that is helping Darwinbox SOC team from proactively detecting any attempts that would potentially compromise customer data integrity.
Round the clock check on rouge services and compromised accounts Is enforced on the IAM layer for each tenant at Darwinbox, this is important in any SaaS provider since every tenant in the multi-tenant architecture is provided with a privilege to define custom integrated open API’s.
Encrypt Data by Default:
Darwinbox cloud stack is enabled with encryption by default for data at Rest which includes both object storage and block storage, Platform security framework governance this adherence. Platform security framework also ensures all data types are clearly defined and are identified with a data classification tag. It is important to store and process data with different level of encryption techniques based on data classification to ensure smooth end user experience. For example, PII data at Darwinbox is end to end encrypted using AES 256 and transactional data is encrypted using Triple DES. At Darwinbox data in transit is encrypted using TLS > 1.2 with authorized strong chippers, platform security framework blocks any requests that are created with unsupported versions like TLS 1.0 and 1.1 during SDLC.
Enforced Data Leak Prevention (DLP):
At Darwinbox DLP software is applied in all layers of tech stack like emails, document management systems, endpoints, and cloud workloads. Platform monitoring framework monitors for sensitive data within Darwinbox HRMS SaaS applications or outgoing transmissions of sensitive data and blocks the transmission. Detection and prevention of sensitive data that is being downloaded to personal devices is monitored and actions like blocking malware or hackers from attempting to access and download data are enforced.


Speak Your Mind