-2.png)

Data security laws are becoming increasingly pertinent in the MENA region. Let’s explore the implications for companies operating in those countries, the importance of data localization, the benefits of complying with local data hosting laws, and how Darwinbox enables data localization for companies in the region.
Data localization is the process of keeping data in the same location where it was created. For example, if a company collects data in Saudi Arabia, it stores it there instead of sending it to another country to be processed. A lot of companies may choose to store data in other countries for cost savings, data backup, access to global markets, or proximity to customers. Since the Internet makes it possible for data to be moved around the world in milliseconds, regulators, privacy advocates, and consumers are becoming more and more interested in where their data goes and what is done with it.
Most data today is saved on cloud servers, and since they can be accessed through the Internet, they can be located in any part of the world. However, data localization is also possible if a cloud provider has a data center in the region the company wants to store the data in, to make sure a customer's data stays in that data center.
Data protection is crucial for safeguarding individuals' privacy and preventing unauthorized access, misuse, or theft of sensitive information, which can lead to financial losses, reputational damage, and legal liabilities for individuals and organizations.
This is why data localization is increasingly gaining importance.
Data Localization Laws in the Middle East and North Africa (MENA) region
Several countries in the MENA region have introduced data localization laws that require companies to store their residents’ personal data within their national borders. These laws are intended to protect the privacy and security of an individual’s personal data and to ensure that it is not subject to unauthorized access or misuse.
The General Data Protection Regulation (GDPR) is a comprehensive data protection law that applies to all member states of the European Union (EU) and the European Economic Area (EEA). It sets strict rules for the collection, use, and storage of personal data, and gives companies and stakeholders the right to control how their data is used. The GDPR outlines general principles for the protection of personal data and requires that personal data be processed in a manner that ensures its security and integrity.
Under the GDPR, personal data may be stored and processed within the EU or EEA, or it may be transferred to a third country, provided that certain safeguards are in place to protect the data. It is important to note that the GDPR applies to the processing of sensitive data, regardless of where the processing takes place. Therefore, if an organization processes employee data in the EU or EEA, it will be subject to the GDPR, even if the data is hosted outside of the EU or EEA.
Here are a few examples of data localization laws in MENA:
Saudi Arabia: In 2018, Saudi Arabia introduced a law that requires all personal data of Saudi citizens and residents to be stored within the country. The law applies to both private and public sector organizations.
United Arab Emirates (UAE): The UAE has implemented data localization laws for certain sectors, such as banking and telecommunications. The laws require companies operating in these sectors to store customer data within the country.
Qatar: In 2016, Qatar passed a law that requires all personal data of Qatari citizens and residents to be stored within the country. The law applies to all companies operating in Qatar.
Egypt: In 2020, Egypt introduced a law that requires all personal data of Egyptian citizens to be stored within the country. The law applies to both public and private sector organizations.
Bahrain: In 2018, Bahrain introduced a data localization law that requires companies to store certain types of data, such as financial and health data, within the country.
It is worth noting that data localization laws in MENA countries may have different requirements and exemptions depending on the sector, type of data, and other factors.
What Does PII Data Localization Mean?
PII data localization refers to the practice of storing or processing Personally Identifiable Information (PII) within a specific geographic location or jurisdiction. PII refers to any information that can be used to identify an individual, such as their name, address, social security number, or email address.
PII data localization laws may require organizations to store PII data within the country or region where it was collected, rather than transmitting or processing it in other locations. This is intended to protect sensitive personal information from unauthorized access, theft, or misuse by foreign entities.
What Are the Benefits of PII Data Localization?
PII data localization can help balance the need for data privacy and security with the need for cross-border data transfer and global business operations. Let’s see how this is done.
1. Enhanced data privacy and security
PII data localization laws can help protect sensitive personal information from unauthorized access, theft, or misuse by foreign entities. This can enhance data privacy and security for individuals, and increase public trust in data-handling practices.
2. Compliance with local regulations
Most companies are subject to laws and regulations that require them to store and manage data of certain types within a specific location. Local hosting helps companies comply with the local regulations.
3. Increased control over data
PII data localization allows countries to exercise greater control over the storage and processing of personal data. This can be particularly important for sensitive data related to national security or public health.
4. Facilitation of cross-border data transfer
In some cases, PII data localization laws may include provisions that facilitate cross-border data transfer while still protecting personal data. For example, the GDPR allows data transfers to countries that provide adequate data protection, or with appropriate safeguards in place.
5. Accessibility and reliability
Locally hosted software platforms offer improved accessibility and reliability. This is particularly important for organizations that require fast access to large amounts of data that can help make informed decisions.
6. Improved transparency
PII data localization can help improve transparency in data-handling practices by requiring organizations to disclose their data storage and processing practices, and by providing more visibility into where data is stored and how it is used.
Darwinbox PII Collection Objects in MENA
Personally Identifiable Information (PII) data localization collection objects refer to the specific types of personal data that are subject to data localization laws. This may include data such as names, addresses, social security numbers, passport numbers, financial information, and health records. Companies must identify the specific PII data that is subject to localization laws in the countries where they operate and take appropriate measures to ensure compliance with local regulations.
PII collection objects in MENA are:
-
Employee Profile Fields
First name, Last name, Email ID, Gender, Marital status, National Identification Card, Passport Number, Iqamah number (a unique identification number that is issued to expatriate workers living in Saudi Arabia. It is also known as a residence permit or residency card number), etc.
2. Attendance Fields
Employee clock-in and clock-out timestamps
3. Payroll Objects
Compensation Structure, Compensation Data, Extra Payments/Deductions
How Darwinbox Uses PII Data Localization For Data Security in MENA
With PII data localization, Darwinbox enables sensitive PII data to be hosted locally within the region. Moreover, this data is encrypted, preventing access or readability in a human-readable format or open text format. This is how the encryption process works:
- All user requests are processed in the tenant's common transactional processor database.
- All the data is encrypted in all databases at all times.
- All operations on PII data are handled in the application logic:
- Data in transit is encrypted with strong ciphers using TLS 1.2.
- When data is saved or updated, it is encrypted using the tenant key before being stored in any database.
- When data is queried, it is decrypted using the tenant key before being sent back to the user.
- Data streams are used to synchronize data in an Online Analytical Processing (OLAP) platform for reporting, in the same encrypted format.
- Data is encrypted in all the databases, like search databases and caches, so it is always in an encrypted format. Darwinbox will not be able to query data in plain text without having access to the tenant key. AES-256 encryption mechanism is used along with the tenant key to encrypt and decrypt data.
The original copy of your PII data resides within the region your company operates in. And when data is in transit, it is end-to-end encrypted, ensuring data security and protection at all times.
PII Data Localization Process Design
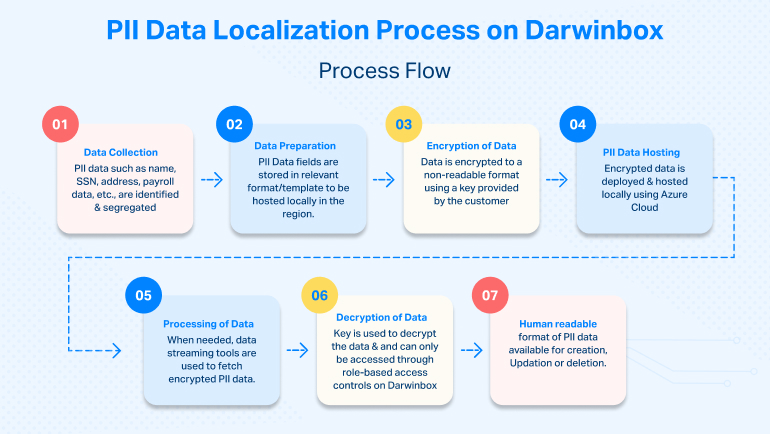
-
Data collection and preparation
Sensitive employee-level details such as first name, last name, social security number, marital status, and salary, etc., are segregated in a master template and stored in a database, so the original copy of the data remains within the geographical region in which the company operates.
-
Data encryption
Data is encrypted in a non-human-readable format using a key provided by the customer. The keys are managed in a vault within the region.
-
Data hosting
The data fields and the encryption keys prepared in the first two stages are deployed within the region, i.e., data is hosted in production in Azure or any other supported cloud center within the region.
-
Data processing
The data stored within the region is accessed by the Darwinbox application to process HR data using decryption. The Darwinbox application communicates with the original copy of the data stored within the region via streaming tools. Data access is also regulated by a role-based data access in Darwinbox, allowing only certain roles to access specified data.
Once data is processed by Darwinbox, it is written in an encrypted format back to the original source within the region. While data is accessed from the company’s local database, it remains encrypted throughout the movement.
Encryption and Privacy Controls on Darwinbox
-
Data transfer encryption
Data is secured while it's being moved using encryption with SSL and TLS1.2 protocols and strong ciphers.
-
Encrypted personal information at the local source
Personal information at the point of storage is encrypted with AES 256-bit encryption.
-
Hashing of credentials
User credentials are hashed with the SHA512 cryptographic hash function for checking and maintaining password integrity.
-
Cryptographic keys
Darwinbox uses an in-house Key Management System (KMS) to manage cryptographic keys to ensure data security and protection.
With the help of these encryption and privacy controls, Darwinbox ensures complete protection and security of data.
The Way Forward
As data becomes an increasingly valuable asset, companies must prioritize the protection of personal information to build long-term relationships with their customers and remain competitive in the global market. Data protection is not only a legal requirement, but it is also a critical element of building and maintaining trust with customers. As local data hosting and data protection laws become increasingly prevalent in many countries around the world, Darwinbox assures end-end data protection for your organization.
Interested in exploring further? Find out how Darwinbox can simplify local data hosting for your organization, book a demo today!


Speak Your Mind